OpenSSL is one of the most powerful tools for managing secure connections and debugging SSL/TLS implementations. In this guide, we’ll break down the use of the command openssl s_client -connect bandit.labs.overthewire.org:31790, explain its purpose, and walk you through how to use it effectively. By the end of this article, even beginners will feel confident using OpenSSL for secure communication tasks.
What Does openssl s_client -connect Do?
The command openssl s_client -connect is a key feature of OpenSSL. At its core, it acts as an SSL/TLS client that establishes a secure connection to a specified server and port. The term “s_client” refers to “secure client.” This command is essential for testing, debugging, and understanding how secure communications work between clients and servers over SSL/TLS.
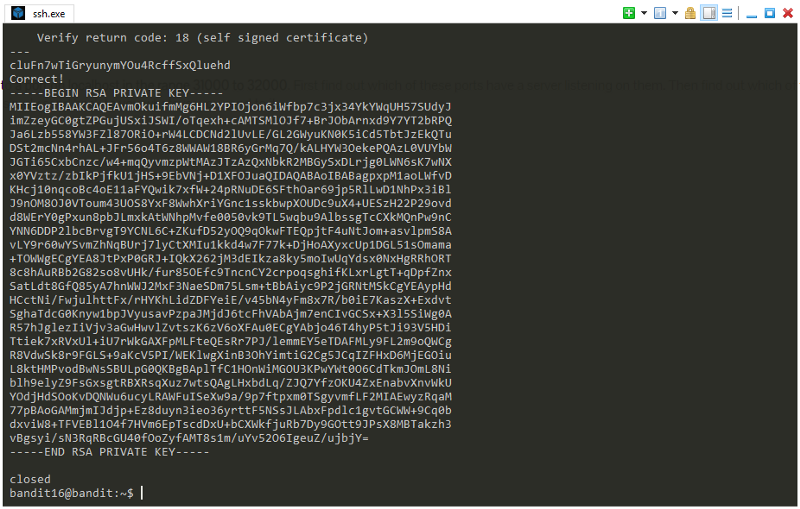
When you run openssl s_client -connect bandit.labs.overthewire.org:31790, it connects your system to the server bandit.labs.overthewire.org on port 31790. This connection simulates an SSL/TLS client-server handshake, allowing you to inspect details such as certificates, supported protocols, and cipher suites.
For example, system administrators often use this command to verify that a server’s SSL/TLS configuration is correct, troubleshoot connection errors, or retrieve SSL certificates.
Why Should You Learn openssl s_client?
Learning how to use openssl s_client is invaluable for anyone working with networks, web applications, or cybersecurity. SSL/TLS is the backbone of secure online communication, ensuring that sensitive data like passwords and credit card information is encrypted during transmission.
Understanding openssl s_client helps you:
- Test and validate SSL/TLS configurations.
- Debug connection issues with servers.
- Extract information about SSL certificates, such as expiration dates or issuing authorities.
- Verify if secure connections to servers are working properly.
Whether you’re an IT professional, a developer, or someone interested in cybersecurity, mastering this command gives you a foundational skill in managing and troubleshooting secure communication protocols.
How to Connect to bandit.labs.overthewire.org:31790
Connecting to the server bandit.labs.overthewire.org on port 31790 using OpenSSL is straightforward. The full command looks like this:
bash
CopyEdit
openssl s_client -connect bandit.labs.overthewire.org:31790
Here’s a step-by-step breakdown of what happens when you run this command:
- The Client Sends a Request: OpenSSL acts as the client and sends a handshake request to the server at the specified domain and port.
- Server Responds: The server responds with details about its SSL/TLS configuration, including its certificate and supported encryption methods.
- Connection Established: If everything is set up correctly, a secure connection is established, and you can view detailed output about the SSL/TLS handshake in your terminal.
This is a simple way to test if the server is reachable and verify its SSL/TLS configuration.
What Happens After Running the Command?
Once you run openssl s_client -connect bandit.labs.overthewire.org:31790, the terminal will display a lot of information, including:
- Details of the SSL certificate, such as the issuer, expiration date, and validity.
- The cipher suite used for the connection.
- Supported SSL/TLS protocols.
You can scroll through the output to examine specific details about the server’s security configuration.
How to Read the SSL Certificate Details
The SSL certificate details are crucial for understanding the security of a server. After running the command, look for sections in the output labeled Certificate chain and Server certificate. These sections provide details about:
- Issuer: The organization that issued the certificate.
- Validity Period: The start and end dates for which the certificate is valid.
- Common Name (CN): The domain or hostname the certificate is issued for.
These details help you confirm whether the server’s SSL certificate is valid and secure.
What If the Connection Fails?
If the connection to bandit.labs.overthewire.org:31790 fails, OpenSSL will display an error message. Common reasons for failure include:
- Server is Down: The server might not be running, or the port might be closed.
- Incorrect Command: Double-check the domain name and port.
- Firewall Restrictions: Your network firewall might be blocking the connection.
By analyzing the error message, you can diagnose and fix the issue.
Troubleshooting Common Errors with OpenSSL
While OpenSSL is powerful, it’s not uncommon to encounter errors when using s_client. Here are a few common issues and their solutions:
- Error: “unable to get local issuer certificate”
- This means the server’s certificate is not trusted. To fix this, you can specify a trusted CA file using the -CAfile option:
- bash
- CopyEdit
- openssl s_client -connect bandit.labs.overthewire.org:31790 -CAfile /path/to/cafile.pem
- Error: “no start line”
- This happens when the input file is not in the correct format. Ensure that your certificate files are in PEM format.
- Timeout Errors
- A timeout error indicates that the server is taking too long to respond. Check if the server is online or if there are any network issues.
What Is OpenSSL and Why Is It Important?
OpenSSL is a widely-used open-source library for implementing secure communication over SSL (Secure Sockets Layer) and TLS (Transport Layer Security). It is the backbone of secure communication protocols and is integrated into most modern operating systems, web servers, and applications.
OpenSSL provides a suite of tools, including s_client, s_server, and x509, to manage SSL/TLS certificates, debug secure connections, and create private keys. Its importance lies in ensuring secure, encrypted communication across the internet. Without tools like OpenSSL, our online data would be vulnerable to eavesdropping and tampering.
Top Tips for Using openssl s_client Effectively
To make the most of the openssl s_client command, keep these tips in mind:

Why Keeping OpenSSL Updated Matters
OpenSSL is constantly updated to patch vulnerabilities and add support for new cryptographic algorithms. Running an outdated version can expose your system to security risks. Always ensure you’re using the latest stable version of OpenSSL by checking your system’s package manager or downloading it from the official OpenSSL website.
Practice with Test Servers
If you’re new to openssl s_client, practicing with test servers is a great way to learn. There are many publicly accessible servers you can use to test SSL/TLS connections without risking sensitive data.
Use OpenSSL for Debugging
OpenSSL isn’t just for testing servers; it’s also a fantastic debugging tool. For instance, you can use the -showcerts option to view all certificates in a chain or the -servername option to specify a hostname during SNI (Server Name Indication) testing.
Thoughts on openssl s_client -connect
The openssl s_client -connect command is an essential tool for anyone working with secure communication protocols. Its ability to connect to servers, inspect SSL certificates, and debug configurations makes it a must-have skill for IT professionals and cybersecurity enthusiasts. By practicing with commands like openssl s_client -connect bandit.labs.overthewire.org:31790, you’ll gain a deeper understanding of how SSL/TLS works and how to troubleshoot issues effectively.
The Bottom Line
OpenSSL is a cornerstone of secure communication on the internet, and the s_client command is one of its most useful tools. Whether you’re testing server configurations, verifying SSL certificates, or debugging connection issues, understanding how to use openssl s_client -connect is a vital skill in today’s digital world.
By following this guide and practicing regularly, you’ll be well on your way to mastering OpenSSL and ensuring the security of your online communications.
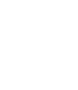










Leave a Reply