Kubernetes is a powerful container orchestration tool, but when it comes to managing user authentication and authorization, integrating Lightweight Directory Access Protocol (LDAP) can make your system both secure and efficient. This guide is designed to help you understand how to get an LDAP profile in Kubernetes in a simple, beginner-friendly way. We’ll explain what an LDAP profile is and why it’s crucial, and we’ll walk you through the steps of integrating LDAP with Kubernetes.
What Is an LDAP Profile in Kubernetes?
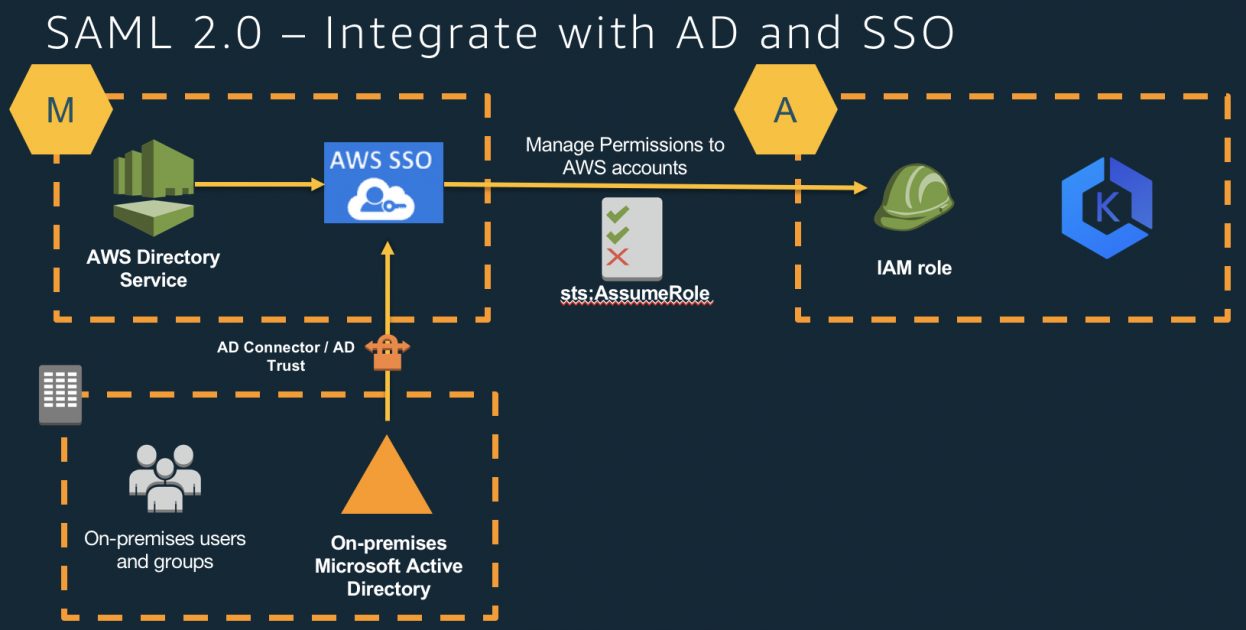
An LDAP profile in Kubernetes refers to the integration of LDAP (Lightweight Directory Access Protocol) with your Kubernetes environment to manage user identities, authentication, and authorization. LDAP is a protocol used to access and maintain distributed directory information services, such as user credentials and organizational hierarchies, over a network. When you connect LDAP with Kubernetes, the cluster authenticates users against a centralized directory instead of managing users locally.
In simple terms, an LDAP profile is like a “directory” that keeps track of user data (like usernames and passwords) so that Kubernetes can verify who is accessing the cluster and what permissions they have. It’s a critical tool for organizations that need a centralized and scalable way to manage users.
Why Is LDAP Important for Kubernetes?
LDAP is a cornerstone for user management in Kubernetes because it simplifies authentication and enhances security. Here are some key reasons why LDAP is important for Kubernetes:
- Centralized User Management: Instead of managing user accounts and credentials separately on each Kubernetes cluster, LDAP centralizes user authentication. This saves time and reduces administrative overhead.
- Scalability: For organizations with large teams or multiple clusters, LDAP ensures consistent user management across all environments, no matter how many users are involved.
- Security: LDAP allows secure authentication using encryption protocols like LDAPS (LDAP over SSL/TLS), reducing the risk of unauthorized access.
- Role-Based Access Control (RBAC): By linking LDAP groups to Kubernetes roles, you can implement RBAC seamlessly, ensuring users only have access to the resources they need.
In essence, LDAP is important for maintaining an organized, scalable, and secure Kubernetes environment.
How Does LDAP Work with Kubernetes?
LDAP works with Kubernetes by acting as an external authentication provider. When a user tries to access the Kubernetes cluster, the cluster checks their credentials against the LDAP server to verify their identity. Here’s a simple breakdown of how it works:

- User Login: A user attempts to log in to the Kubernetes cluster using their credentials (username and password).
- LDAP Server Validation: Kubernetes sends these credentials to the LDAP server for validation.
- Authorization: Once the user is authenticated, Kubernetes maps the user to specific roles or permissions based on their LDAP group.
- Access Granted: The user gains access to the cluster with the appropriate permissions.
This process allows Kubernetes to rely on LDAP for user management while focusing on container orchestration tasks.
Benefits of LDAP Profiles in Kubernetes
Integrating LDAP profiles with Kubernetes offers several advantages, including:
- Simplified User Authentication: Centralized authentication through LDAP reduces complexity and improves efficiency.
- Seamless Role Mapping: LDAP groups can be mapped to Kubernetes roles, enabling fine-grained access control.
- Enhanced Security: LDAPS ensures secure communication between Kubernetes and the LDAP server.
- Scalability: Easily manage thousands of users and groups without compromising performance.
- Audit and Compliance: LDAP logs user access, making it easier to meet compliance requirements.
Steps to Get an LDAP Profile in Kubernetes
Getting an LDAP profile in Kubernetes involves several steps. Here’s a detailed guide to help you through the process:
- Set Up an LDAP Server: If you don’t already have one, set one up using tools like OpenLDAP or Active Directory.
- Configure Kubernetes Authentication:
- Modify the Kubernetes API server to use an external authentication webhook.
- Set up the webhook to connect to your LDAP server.
- Install and Configure a Webhook Authentication Server: The webhook acts as a bridge between Kubernetes and your LDAP server. You can use tools like Dex, an open-source OIDC identity provider, to set this up.
- Map LDAP Groups to Kubernetes Roles: Create RoleBindings or ClusterRoleBindings to assign Kubernetes roles to LDAP groups.
- Test the Setup: Use a test user to ensure the LDAP profile is working as expected.
These steps ensure that your Kubernetes cluster is configured to authenticate users against an LDAP server.
Setting Up Your Kubernetes Environment for LDAP
Before integrating LDAP, you must ensure your Kubernetes environment is ready. Here’s how you can prepare:
- Update Your Kubernetes Version: Ensure you’re running a version of Kubernetes that supports external authentication (1.13+).
- Install Required Tools: Install kubectl (Kubernetes CLI) and other tools like Helm if needed.
- Configure Network Settings: Ensure your Kubernetes cluster can communicate with the LDAP server. Open the necessary ports (e.g., 389 for LDAP and 636 for LDAPS).
- Set Up Certificates: If you’re using LDAPS, configure SSL/TLS certificates for secure communication.
With these preparations, your environment will be ready for LDAP integration.
Common Issues When Getting an LDAP Profile in Kubernetes
While setting up an LDAP profile in Kubernetes, you may encounter some common challenges:
- Connection Errors: Kubernetes may fail to connect to the LDAP server due to incorrect network configurations or firewall restrictions.
- Misconfigured Roles: Improper mapping of LDAP groups to Kubernetes roles can result in users having incorrect permissions.
- Certificate Issues: If you’re using LDAPS, expired or invalid SSL/TLS certificates can cause authentication failures.
- Slow Authentication: High latency between the Kubernetes cluster and the LDAP server can slow down the authentication process.
Understanding these issues beforehand can help you troubleshoot more effectively.
Troubleshooting Connection Errors
Connection errors between Kubernetes and the LDAP server are among the most common problems. Here’s how you can troubleshoot them:
- Check Network Connectivity:
- Use tools like ping or telnet to ensure Kubernetes can reach the LDAP server.
- Verify that the necessary ports (389 for LDAP, 636 for LDAPS) are open.
- Validate Configuration:
- Double-check the LDAP server URL, username, and password in your Kubernetes configuration files.
- Ensure that the API server is configured to use the authentication webhook correctly.
- Review Logs:
- Check the logs for both Kubernetes and the LDAP server for error messages.
- Look for errors like “connection refused” or “authentication failed.”
- Test with a Simple LDAP Client:
- Use an LDAP client (like ldapsearch) to test connectivity and authentication independently of Kubernetes.
By addressing these issues, you can resolve most connection errors quickly.
Testing Your LDAP Profile Setup
After setting up LDAP, it’s crucial to test the integration to ensure everything is working as expected. Here’s how:

- Login Test: Try logging into the Kubernetes cluster using LDAP credentials.
- Role Verification: Check whether the user has the correct roles and permissions assigned.
- Group Mapping: Confirm that LDAP groups are correctly mapped to Kubernetes roles.
- Audit Logs: Review Kubernetes and LDAP logs to verify successful authentication events.
Testing ensures that your LDAP profile is fully functional and ready for production use.
Best Practices for Using LDAP Profiles in Kubernetes
To get the most out of your LDAP integration, follow these best practices:
- Use LDAPS: Always use LDAPS (LDAP over SSL/TLS) for secure communication between Kubernetes and the LDAP server.
- Regularly Update Certificates: Keep SSL/TLS certificates up to date to avoid authentication failures.
- Monitor Performance: Use monitoring tools to track LDAP server performance and address latency issues.
- Implement RBAC: Use Role-Based Access Control to limit user permissions based on their roles in the organization.
- Backup LDAP Data: Regularly back up your LDAP server to prevent data loss in case of a failure.
Following these practices will ensure a secure and reliable LDAP integration with Kubernetes.
Can I Use LDAP Without Kubernetes?
Yes, LDAP can be used without Kubernetes. LDAP is a standalone protocol designed for user authentication and directory services. Many organizations use LDAP with other applications like web servers, email systems, or VPNs. However, integrating LDAP with Kubernetes adds value by centralizing user management in containerized environments.
Is LDAP Necessary for All Kubernetes Projects?
LDAP is not necessary for all Kubernetes projects. Small teams or projects with minimal user management requirements might not need LDAP. However, for larger organizations or projects with strict security and scalability needs, LDAP is a vital tool for effective user authentication and authorization.
The Bottom Line
Integrating an LDAP profile into your Kubernetes cluster enhances security, simplifies user management, and enables scalability. By following the steps outlined in this guide, you can successfully set up and use LDAP in your Kubernetes environment. Whether you’re managing a small team or a large organization, LDAP integration ensures efficient and secure user authentication. Always test your setup thoroughly and follow best practices to maintain a robust and reliable system. With LDAP and Kubernetes working together, you’ll have a secure and streamlined infrastructure ready to support your applications.










Leave a Reply